User provisioning
Last updated: Mar-04-2026
If your account has multiple users, you can use roles to control access and permissions within the Console, in line with your data and asset governance policy.
Start by identifying key workflows, assets, and resources that each user needs to access, as well as actions they should be able to perform. Once you've analyzed your organization's governance needs, you can set access and permission levels for each user in the following ways:
-
User roles: Assign each user a role to control their access to areas of the Cloudinary Console.
- The account creator automatically receives the Master admin role, with full permissions for all product environments. This role should typically be limited to one or a few users.
- Developers often use Admin or Technical admin roles for access to API keys and development tasks. Additional roles are available for billing, reporting, and managing Assets users and admins.
- Users assigned the Media Library user role can access the Media Library. However, the content they can access is restricted to the folders and collections that are shared with them. This ensures users can only access relevant content.
User groups: Simplify access control for Media Library users and the content they can access within the Media Library by managing permissions for multiple users at once, rather than individually. After configuring groups, assign them access to specific folders and collections. For more details, see the Assets users and group management documentation.
- Every user who accesses the Console requires a separate seat license.
- Users and user groups are configured on the account level, so you can manage them from within any of your product environments.
- Users with the Master admin role have access to all product environments. Users with all other roles can be given access to all or to only selected product environments.
Provisioning API
This guide focuses primarily on provisioning users from the User Management page of the Cloudinary Console. However, accounts with access to the Provisioning API can also create and manage users and user groups programmatically using the RESTful Provisioning API.
Provisioning API access is available for accounts on an Enterprise plan. If you don’t currently have access and would like to explore your options, contact us.
The Provisioning API uses Basic Authentication over HTTPS. Your Account API Key and Account API Secret are used for the authentication. These credentials (as well as your ACCOUNT_ID) are located in the Account API Keys page of the Console Settings.
The Provisioning API provides the following capabilities:
User configuration endpoints: Manage users by retrieving a list of users and details of a single user, creating a user, updating details, or deleting users.
User group management endpoints: Manage user groups by creating groups, updating group details, retrieving a list of groups, retrieving group information including a list of members, adding or removing users, and deleting groups.
For more details, see the Provisioning API reference.
User configuration
The My Profile page of the Console Settings, which you can navigate to by clicking the gear icon in the Console Options sidebar, includes your personal user profile details, email preferences, and two-factor authentication setup. Account users with any role can update personal information here.
As a user with a Master admin or Admin role, you can also configure settings that impact all account users as well as the option to add or modify individual users and permissions:
- You can view and manage all account users, including adding users, removing users, changing their roles, and more.
- You can activate SAML login for your organization from the Account Security page of the Console Settings.
Root user
The Root User is automatically created in a Cloudinary account as the first user and holds permanent, full administrative access. This user is essential to account management, is clearly marked in the interface, and is the only user who can cancel the account. The Root User is subject to the following restrictions:
Can't be deleted, disabled, force-logged out, or have its password revoked
Can't be assigned to roles
Is always assigned to all product environments
Having a root user ensures there is always a reliable point of authority with full access to manage and maintain the account.
Managing users
You can manage account users within the Console in one of the following ways:
- Via the Invite New Users Console option
- From the User Management page within your Console Settings
- Automatically, using SAML provisioning with any SAML-compliant identity provider
Adding users
You can add up to five users at a time (depending on how many users your plan allows) by either:
- Using the Invite New Users Console option
- Clicking the Invite button from the User Management page within your Console Settings
For each user, you can set:
-
E-mail: After creating a new user, that user will receive an email that requires confirmation to this address. This email address is also used for logging in to Cloudinary. NoteIf you'd like to prevent users with email addresses on your domain from signing up for separate free accounts, which would prevent you from adding them to your main account as a user, please contact support.
- Role: Controls which areas the user can access and which operations they can perform in those areas. For details, see Role-based permissions below.
The following permission levels apply to all new users with common roles, as described below. If you want your new users to have different permissions or levels of access, you need to complete a separate form for each:
-
Product environment access1: If your account includes more than one product environment, you can define which product environments all the new users can access.
- Users with the Master admin role always get full control in all product environments, so this option is displayed only when you're adding at least one user with a role other than Master admin.
- By default, users are granted access (at the same role level) to all product environments, even if your account has more than 30. If you'd prefer to limit access, clear the checkbox to manually select up to 30 product environments.
Additional options for users with the Media Library user role:The Media Library user role is typically assigned to Assets (Digital Asset Management) users who manage content in the Media Library. For more details on additional options related to the Media Library user role and the actions they can perform, see Media Library user role in the Assets Admin Guides.
Updating users
To update details for an individual user, including user name, email, and permissions, select Edit from the kebab menu at the end of a specific user's row on the User Management page in your Console Settings. A form opens that allows you to update the information for a single user at a time. Cloudinary re-sends the user an invite, which is especially useful after updating a user's information.
To modify the product environments assigned to a user, click the entry in the Product Environment column to open the Assign Product Environments form.
- If a user is a Master admin, the value in the Product Environment column is All, indicating full access. You can't edit this value without first changing the user's role.
- You can assign a user access to All product environments, even if your account has more than 30. If you prefer to restrict access, you can manually select up to 30 specific environments.
For a full explanation of user permissions you can update, see Adding users.
Resetting user passwords
You can initiate a password reset for an individual user to ensure account security.
To initiate a password reset, select Reset Password from the kebab menu at the end of a specific user's row in the User Management page within your Console Settings. This action:
- Immediately terminates the user's active session.
- Invalidates the old password, rendering it unusable for login. The user must set a new password to regain access.
- Triggers an email containing a link that allows the user to set a new password. Alternatively, users can initiate the password reset process themselves by clicking on the Forgot your password link on the login page.
Users undergoing a password reset are marked with a specific status in the User Management table, clearly indicating that they are in the process of changing their password. This makes it easy to identify and manage such users.
Force immediate logout
You can initiate a force logout for an individual user to ensure account security. This feature is particularly helpful when you prefer not to require a password reset, or for users logged in via Google, GitHub, or SAML, who lack passwords, making it impossible to link session termination with a password reset.
To force a user to logout, select Force Logout from the kebab menu at the end of a specific user's row in the User Management page within your Console Settings. This action terminates the user's active session within ten minutes.
Deleting users
To delete a user, select Delete from the kebab menu at the end of a specific user's row in the User Management page within your Console Settings.
Alternatively, Enterprise customers with access to the Provisioning API can disable users programmatically using the Delete user endpoint.
When a user leaves your organization and needs to be removed from your system, certain information about them must still be retained. This includes details like the collections they created and the assets they uploaded.
To address those needs, user deletion is handled in the following ways:
- The deleted user's status is changed to Inactive on the User Management page in the Console Settings. This status is permanent, and the user can't be reactivated.
- Throughout the user interface, a label indicating Inactive is displayed wherever the deleted user is mentioned.
- Deleted users no longer count against your account's user quota.
- You have the option to reuse the deleted user's email and assign it to a completely new user.
Managing additional user subscriptions
You can see the maximum number of users that you're eligible for via your base plan in the panel on the right side of your Account Settings page of the Cloudinary Console. If you need to increase your user limit, you can upgrade your plan by clicking the Change Plan button.
Alternatively, you can purchase additional user subscriptions over and above your plan's limit. If you've reached the maximum number of users allowed for your plan, a banner will appear in the User Management page within your Console Settings. Click the Change user limit link displayed in the banner. You can extend your limit by up to 20 additional user subscriptions, with no need to switch plans.
Afterwards, you can increase or decrease the number of additional user subscriptions on your account anytime.
For additional help, or to add more than 20 additional users, contact support.
Role-based permissions
Each user in your Cloudinary account is assigned a role. This role defines the operations a user can perform, the areas of the Cloudinary Console that they can view or change, and the settings they can control.
Whereas Master admins have access to all product environments, users with other roles can be set to have access to all or only specified product environments. Users have the same role in all product environments they have access to.
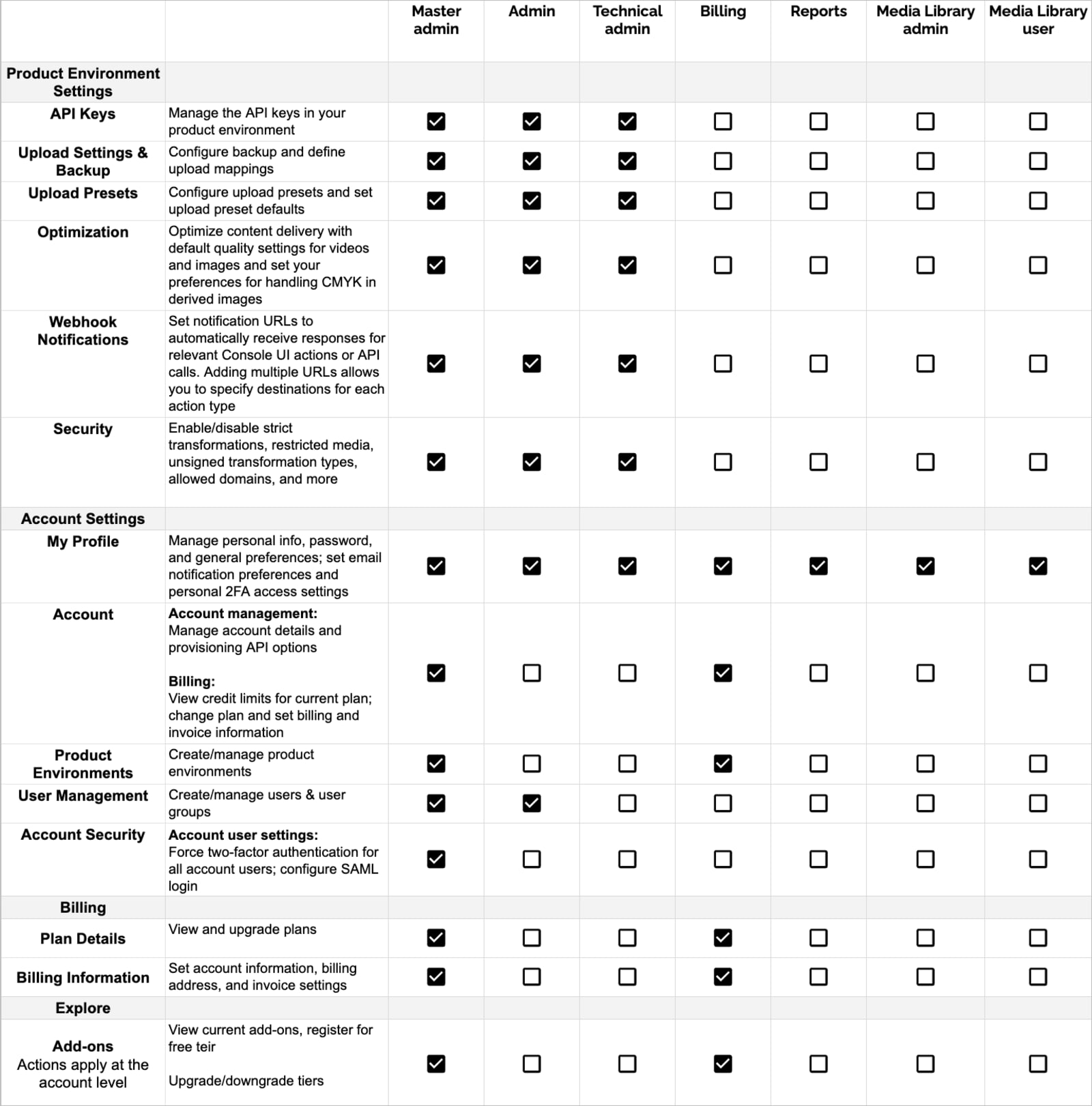
Below are tables summarizing the permission details for each role, divided by Console areas:
Permissions for Console Pages
- Master admin, Admin, and Technical admin roles can access every page of the Console.
- Billing and Reports roles can access only the dashboard and reports located in the Home area of the Console.
- The Media Library admin role can access the Media Library for full usage and administration.
- The Media Library user role can access specific folders and collections within the Media Library according to their assigned permissions.
Permissions for Console Settings
SAML/SSO login
Find the option to activate SAML (SSO) login in the Account Security page of the Console Settings:
SAML Login: This option enables the administrator to activate SAML (SSO) login. This can enable users in your organization to log in using the same authentication system that they use for other SSO-supported applications. If you activate this option, you can globally select whether to Enforce SAML login or to allow users to choose whether to log in either via the SSO application or via the Cloudinary Console login window. If you choose the latter ('Enforce' is disabled), then when creating new users, you can optionally select Send invitation email for that user. When selected, that user receives an email inviting them to create a Console password.
- If your account has SAML (SSO) login enabled and you use the Media Library Widget or one of our Integrations, you must allowlist the domain
console.cloudinary.com. If you need assistance, contact Support. - If you also use the [SAML Provisioning][saml-sso-provisioining] feature, make sure the Two-Factor Authentication user setting (2FA) is Disabled. You can configure two-factor authentication through your IdP, if required.
- The two-factor authentication (2FA) user setting is ignored when using SAML login to log in to Cloudinary, as the SSO IdP is trusted.
- Even if you set Enforce SAML login to Enabled, any user created with the Master admin role will automatically get an invitation to set a Console password and will be able to log in directly to the Console, if needed.
 Ask AI
Ask AI